Hikvision Security Vulnerability
Are Hikvision Cameras Vulnerable to hackers?
How to evaluate the risks of my Hikvision devices?
To exploit this vulnerability, an attacker must be on the same network as the vulnerable device. In other words, if the attacker to view the login screen of a vulnerable device, they could attack it. If they cannot get to the login screen of a vulnerable device, they are not able to exploit the vulnerability.
To evaluate the risk level of a vulnerable device, check if the affected model exposes its http/https servers (typically 80/443) directly to the Internet (WAN), which would give a potential attacker the ability to attack that device from the Internet.
Below are some examples:
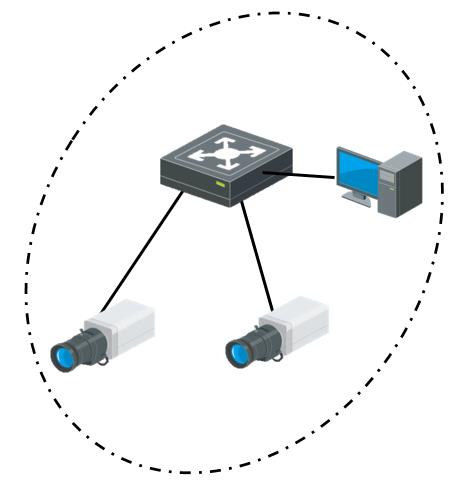
① LAN network without Internet access (low risk)
A potential attacker cannot access the device’s web server from the Internet so the risk is low (attacker must have LAN access to exploit this vulnerability, that’s what we mean with low risk)
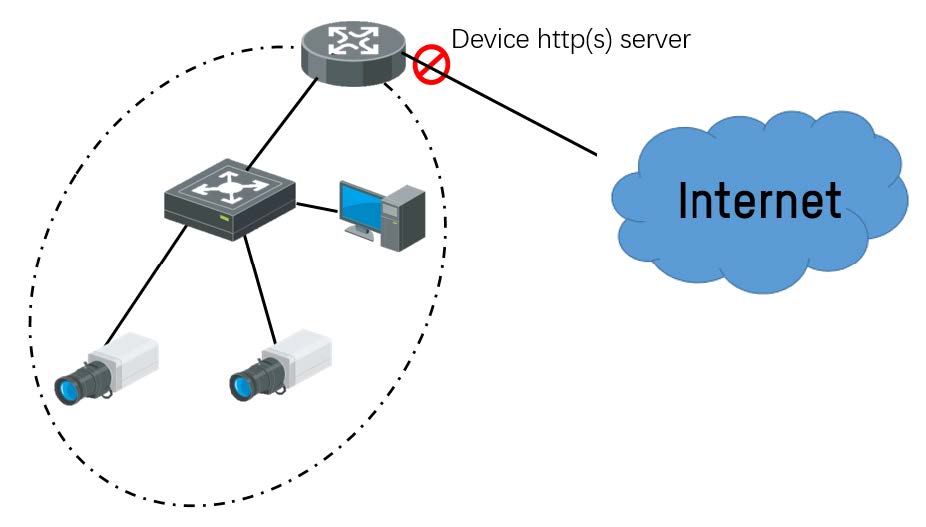
② WAN network with firewall blocking device http(s) server (low risk)
Since potential attacker still cannot access device web from Internet, this situation the system is still considered low risk
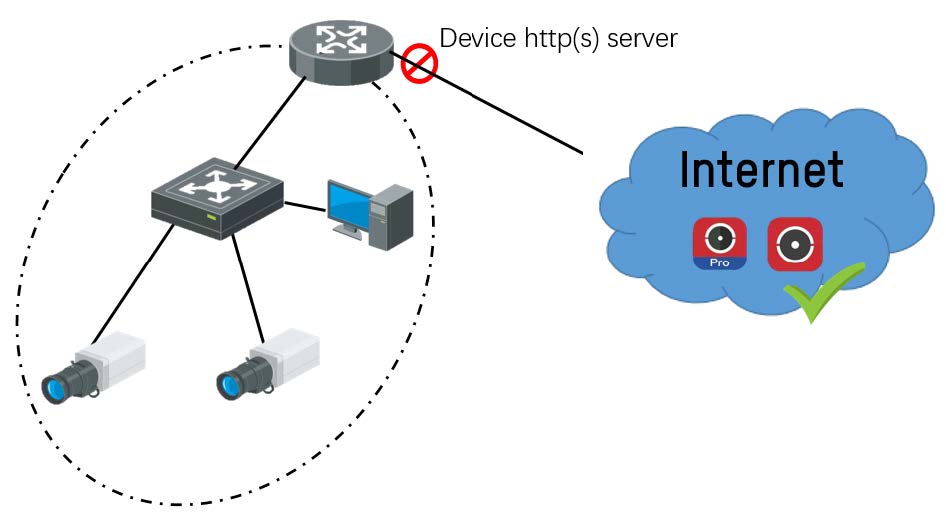
③ Hik-Connect & Hik-ProConnect (low risk)
HC and HPC are special case of above second scenario, http(s) is not needed in HC/HPC service so it will be as safe as usual
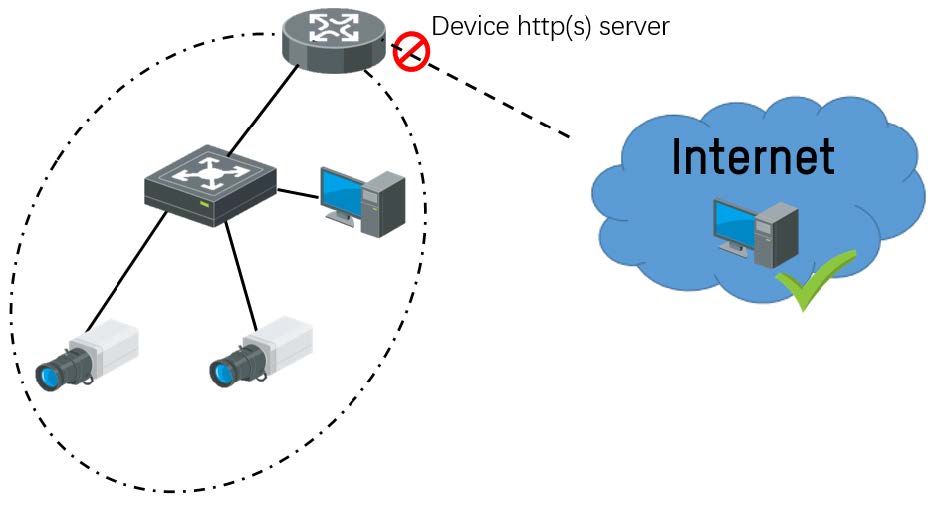
④ VPN access from Internet (low risk)
VPN (Virtual Private Network) allows only verified users to login and access devices from site network, so it’s a secured way to access device and not easy to be attacked
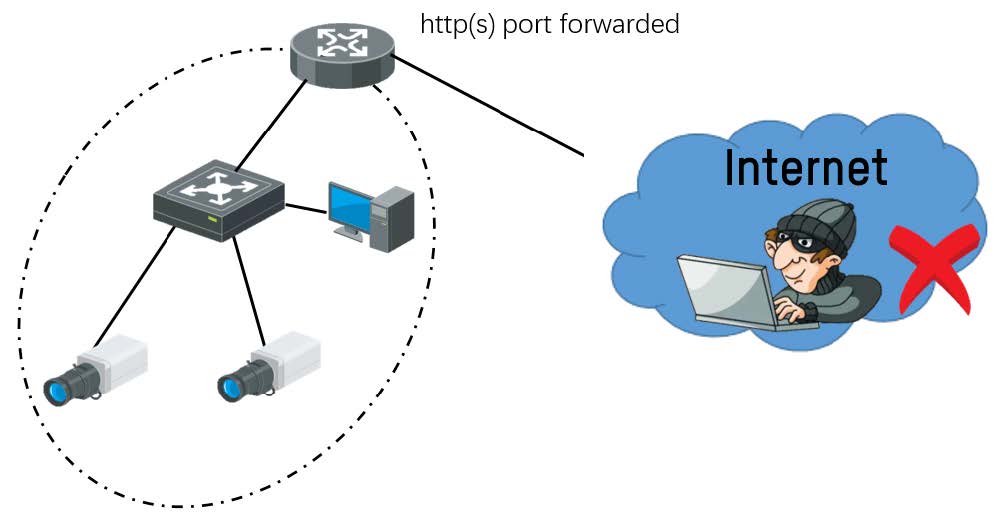
⑤ Port forwarding (High Risk)
Port forwarding is easy and inexpensive way for users to remotely access a device, however port forwarding brings additional risks because it tells the firewall not to block traffic to that device from the Internet on certain ports. Therefore, with current vulnerability, as long as a potential attacker has access to a device through its forwarded http(s) ports, the device is at high risk of been attacked.
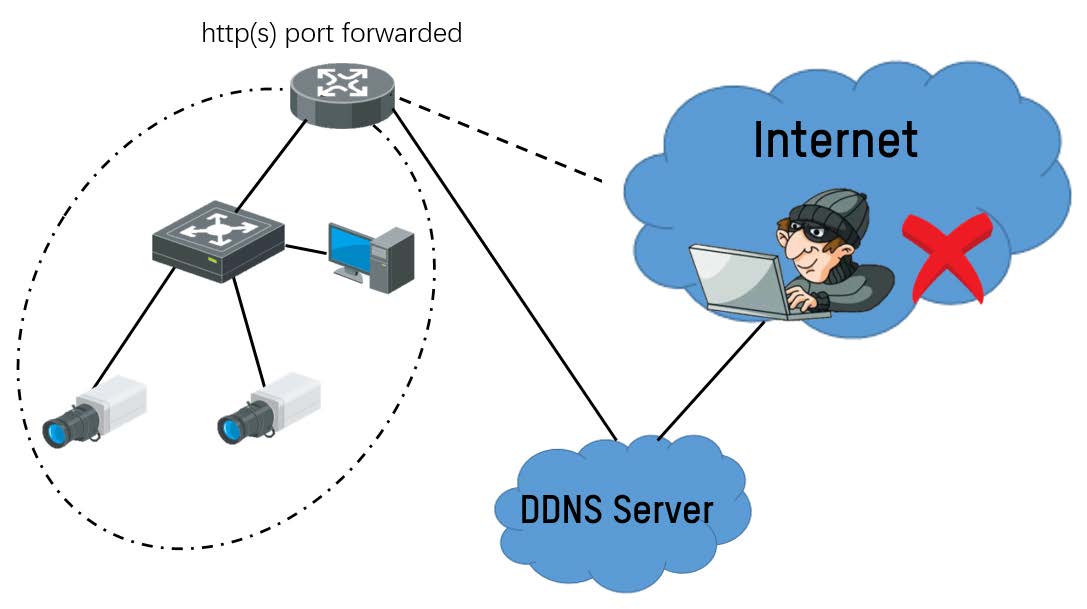
⑥ DDNS (High Risk)
Dynamic DNS (DDNS) also uses port forwarding so a potential attacker could still have access to device from the Internet, putting device high risk of been attacked.
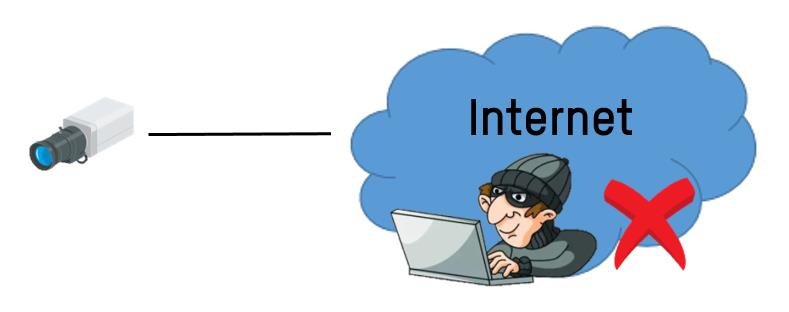
⑦ Direct WAN Access (High Risk)
Some sites install devices directly to Internet (WAN). As long as the device has an open IP address and its http(s) ports are exposed to Internet, the device is at high risk of been attacked.
In brief conclusion, the easiest way to evaluate system risk level is to check if you can access device webpage directly without any extra network variation. If yes, the system should be considered at high risk.
As far as we know, the only people who know how to exploit this vulnerability are the researcher and Hikvision’s HSRC. However, now that the patch has been released and attackers know that this vulnerability exists, they will be searching for it. If you have an affected camera/NVR whose http(s) service is directly exposed to the Internet, Hikvision highly recommends you to patch your device immediately (recommended), and using a more secure solution, like a VPN.
NOTE: This document addresses the risk of Internet attack. It assumes that your internal network is properly segmented and that a threat actor has not gained access to your internal network. To further assess risk, determine if your internal network is trusted and if not, take the proper measures to patch and segment your video surveillance network from other parts of your internal network.
Sharing is caring:
You might also like
Security Perth Blog | Get Security Tips and advice from your local experts.